Website Malware Protection - An Overview
Word Press, and its plugins, is no various. Not upgrading your styles and plugins can mean difficulty. Many hackers rely on the simple fact that individuals can't be bothered to upgrade their plugins and themes. More often than not, those hackers make use of bugs that have currently been fixed. So, if you're utilizing any Word Press item, upgrade it regularly. Along with many other functions and enhancements to your Word Press security, quality handled hosting offers automatic updates for all aspects of your Word Press site. Some managed hosting providers consist of Kinsta, Site Ground, and Flywheel. You can find out more about the top managed Word Press hosting here. Your existing Word Press version number can be discovered really easily.
You can likewise see it on the bottom of your dashboard (but this doesn't matter when trying to secure your Word Press site). Here's the Click to find out more important things: if hackers understand which version of Word Press you use, it's easier for them to tailor-build the ideal attack. You can conceal your variation number with practically every Word Press security plugin that I discussed above.
Nevertheless, whatever that I mentioned in this article is a step in the right instructions. The more you care about your Word Press security, the harder it gets for a hacker to break in. However, with that being said, probably similarly as important as security is site performance. Basically, without a site that loads rapidly, your visitors will never get a possibility to consume your content.
Here are some resources that can help you win the efficiency game and ensure that your site loads lightning quick: If you have any concerns on how to secure your Word Press website, let us understand in the remarks and we'll answer them! So what are your Word Press security obstacles?.
The 9-Second Trick For Protecting Website From Malware
We were losing a lot of valuable time cleaning websites ourselves. We were looking for a partner to outsource the cleansing up of malware to. 3 things was very important to us: The cleanups need to be comprehensive and fast, the procedure to request a clean-up ought to be simple, and the costs need to be sensible for us and our customers.-- Gijs Hovens.
A worldwide CDN and cloud-based security for your website to supercharge the performance and protect from online threats. SUCURI WAF safeguard http://www.thefreedictionary.com/protect your webiste from malware from OWASP top 10 vulnerabilities, strength, DDo S, malware and more. Make your website load much faster by as much as 70%. Attempt SUCURI
Authored by a Symantec staff member The majority of individuals are uninformed of the reality that you do not need to purposefully download a malicious attachment in order to compromise your computer system's security. Harmful websites and drive-by downloads are simply two ways that your security can end up being compromised by doing absolutely nothing more than checking out a website.
And regardless of what you may have heard, Macs need them simply as much as Windows devices. A malicious site is a website that tries to install malware (a general term for anything that will interrupt computer operation, collect your individual info or, in a worst-case circumstance, gain total access to your device) onto your gadget.
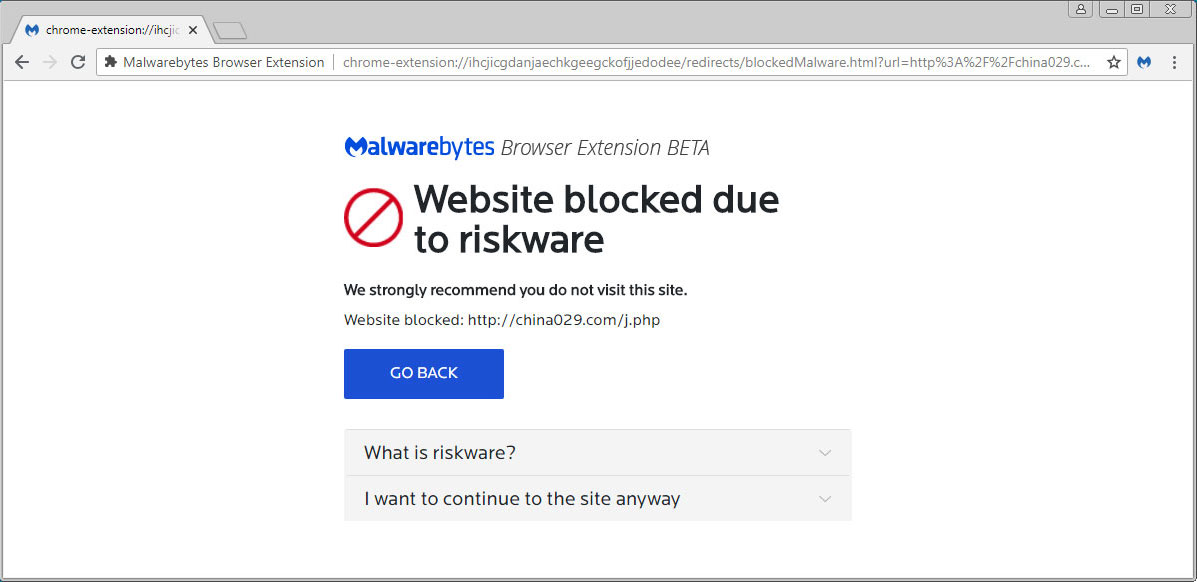
Not known Details About Protecting Website From Malware
What's more, destructive websites often look like legitimate websites. Sometimes they will ask you to set up software application that your computer appears to need. For example, a video website might ask you to set up a codec, which is a little piece of details a video player needs to run on a site.
Similarly, the website might ask for consent to set up one program, however install an entirely different one-- one that you absolutely do not want on your computer system. Drive-by downloads are even scarier than a destructive website, though the 2 sometimes overlap. Drive-by downloads can be set Discover more here up on your computer merely by taking a look at an e-mail, searching a site or clicking a pop-up window with text developed to mislead you, such as a false mistake message.
What's more, your anti-virus software might be incapable of identifying it, because hackers deliberately make it tough for anti-virus software application to identify. Drive-by downloads often do not need your approval, or deceiving you into offering it. Sometimes the harmful code conceals deep in the code of the website. Once the download is on there, it can be challenging or impossible to leave of your computer system, tablet or cellphone.
There are a great deal of dangers out there and malicious websites hosting drive-by downloads are some of the most recent and scariest. But there are ways for you to protect yourself so that you can utilize the Internet without difficulty. Do your due diligence and exercise reasonable care and your web browsing should be smooth cruising.
Facts About Protection From Malware Revealed
We 'd like to think that the Internet is a safe and sincere location for everyone, but there's no rejecting that online bad guys and hackers are prowling out there, attempting to trigger difficulty. One method that they trigger trouble is by spreading malware. You can secure yourself by discovering what malware is, how it spreads and how to avoid it.
Malware can steal sensitive details from your computer, gradually slow down your computer system or perhaps send out phony emails from your e-mail account without your knowledge. Here are some common kinds of malware that you might have found out about: Virus: A harmful computer system program that can copy itself and contaminate a computer system.
Spyware: Malware that gathers information from people without their understanding. Adware: Software that instantly plays, shows or downloads ads on a https://www.washingtonpost.com/newssearch/?query=protect your webiste from malware computer. Trojan horse: A destructive program that pretends to be an useful application, but damages your computer system or takes your information after it's set up. How malware Web Security spreads Malware can get onto your computer system in a variety of different methods.
Now that you understand what malware is and what it can do, let's review some practical steps that you can require to safeguard yourself. How to avoid malware Keep your computer and software updated Microsoft and Apple frequently launch updates for their operating systems, and it's an excellent concept to set up these updates when they end up being readily available for your Windows and Mac computers.
The Malware Statements
Some operating systems also use automated updates, so that you can automatically get updates soon after they're readily available. Windows users can install updates utilizing a feature called "Windows Update", while Mac users can set up updates utilizing a function called "Software Update". If you're not knowledgeable about these functions, we encourage you to browse the Microsoft and Apple websites to find out more on how to set up system updates on your computer.
More recent variations often include more security fixes to avoid malware attacks. Utilize a non-administrator account whenever possible Most os allow you to produce several user accounts on your computer system, so that different users can have various settings. These user accounts can likewise be set up to have various security settings.